Trusted by thousands of companies worldwide






How it Works
How SecureTrustCyber Security Solution Works
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Advanced Detection
Our system continuously monitors your network and data environments for any suspicious activities.
Robust Data Encryption
We ensure that all sensitive data is encrypted and at rest, using industry-standard encryption protocols.
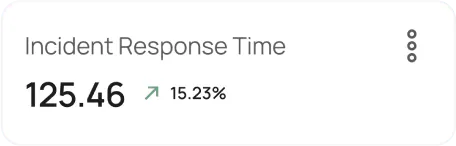
Automated Response
In the event of a security incident, our automated response system takes immediate action.
Key Features
In-Depth Explanation of Our Web Security Features
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
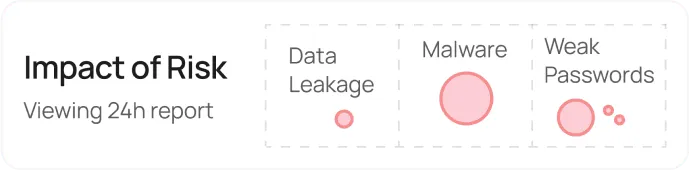
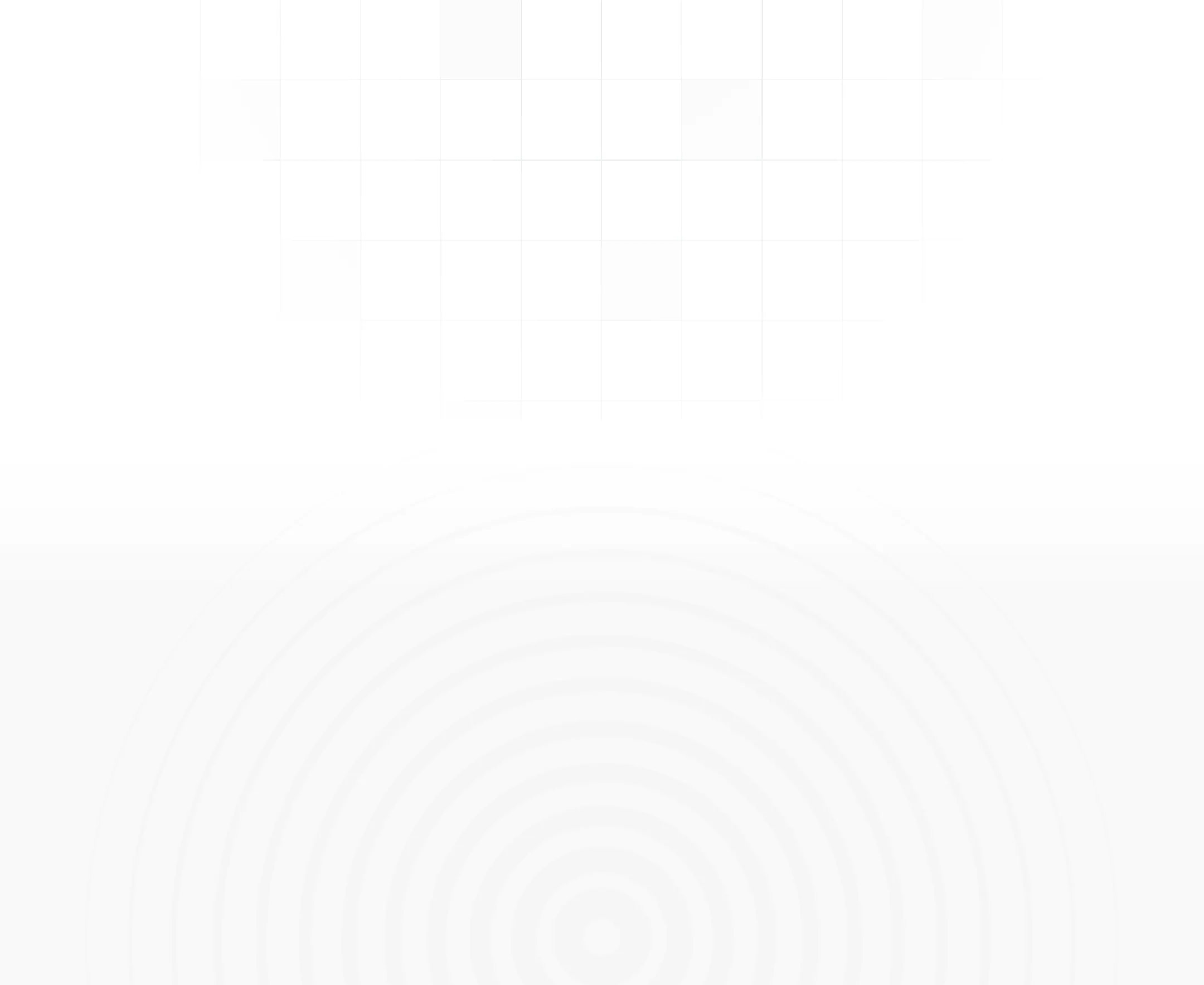
Continuously evaluates potential security threats and impact
This includes suggesting security patches, policy updates, and other preventive measures to reduce the likelihood and impact of threats.
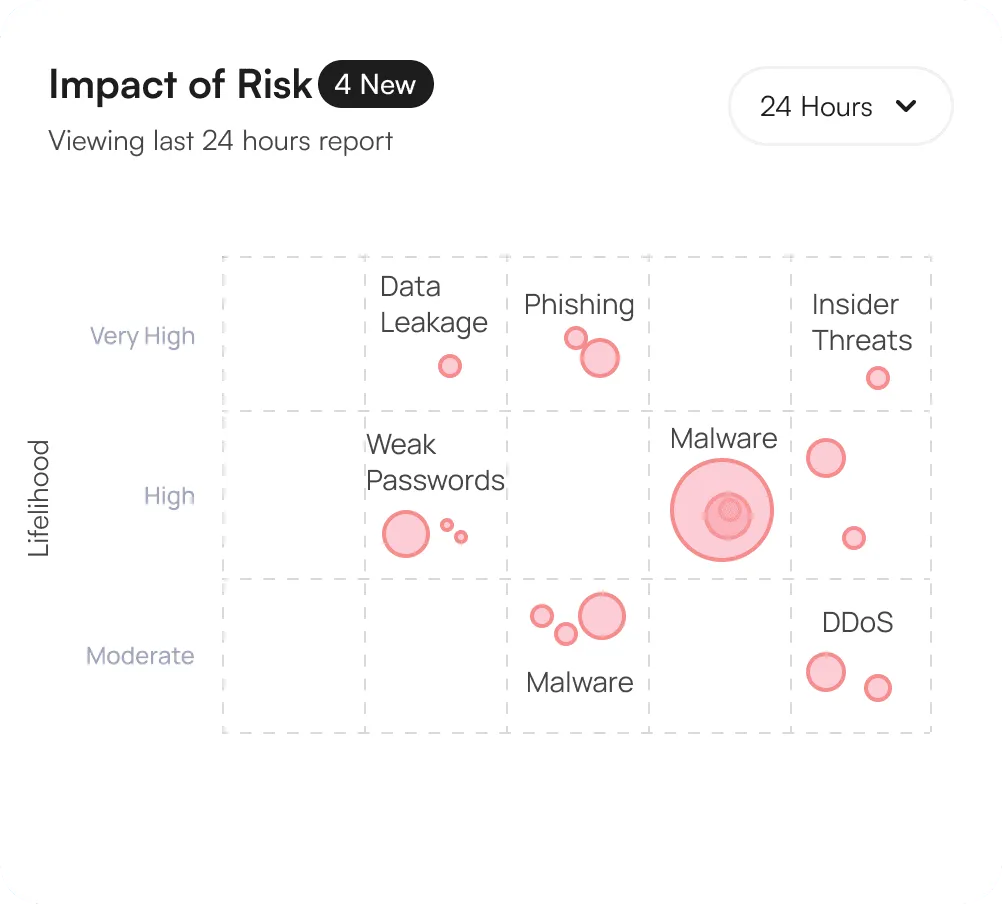
Presents a view of your organization security posture
Allows you to set thresholds for security parameters and receive real-time alerts when these thresholds are breached ensuring you stay informed of critical events.
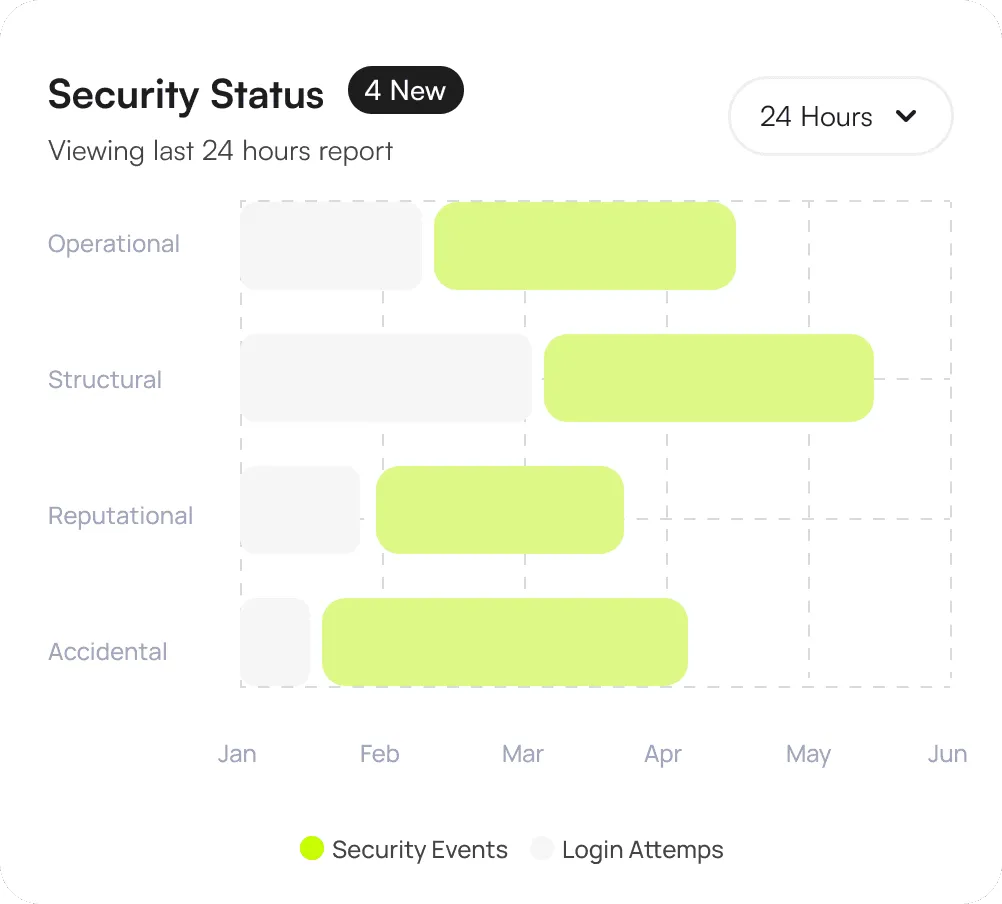
Monitors and logs all the data access events
Monitors and logs all data access events, including who accessed what data, when, and from where. This provides a clear audit trail for compliance and security investigations.
Learn More Details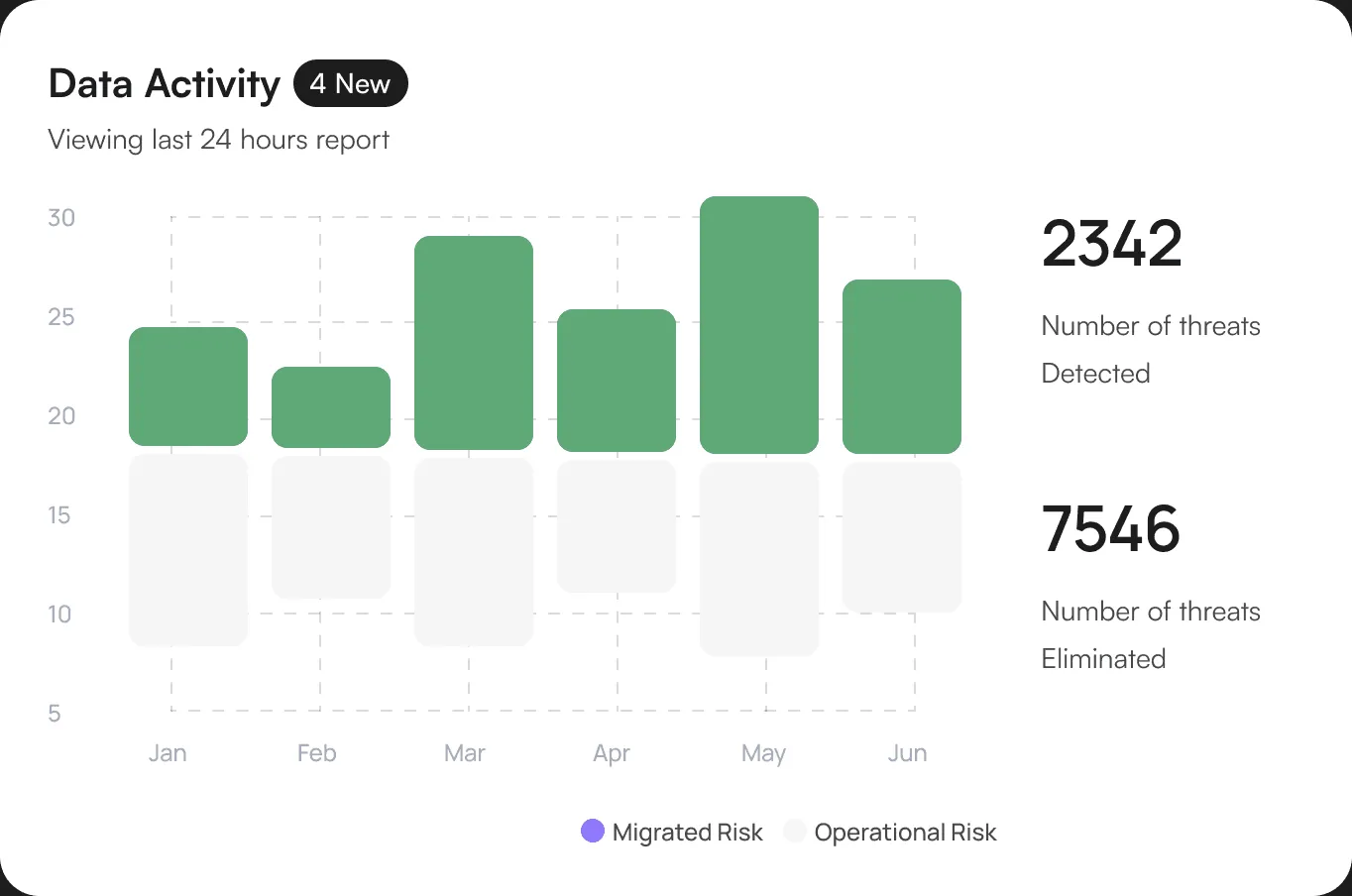
Essential Feature
Discover the Features That Makes SecureTrustCyber Stand Out.
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Threat Prevention
Our advanced threat prevention capabilities keep you safe from a wide range of cyber threats.
Firewall-as-a-Service (FWaaS)
Cloud-delivered firewall to protect all your users and devices.
Secure Web Gateway (SWG)
Block threats and control internet access with our secure web gateway.
Intrusion Prevention System (IPS)
Prevent network intrusions with our advanced IPS technology.
Malware Prevention
Stop malware in its tracks before it can infect your systems.
DNS Security (DNS)
Secure your DNS traffic and prevent access to malicious domains.
Remote Browser Isolation (RBI)
Isolate web browsing activity to protect your network from web-based threats.
Data and App Protection
Protect your sensitive data and applications with our comprehensive security solutions.
Cloud Access Security Broker (CASB)
Gain visibility and control over your cloud apps and data.
Data Loss Prevention (DLP)
Prevent sensitive data from leaving your network.
Zero Trust Network Access (ZTNA)
Provide secure access to your applications based on a zero-trust model.
AI Security (AISEC)
Leverage AI to detect and respond to threats in real-time.

Detection and Response
Detect and respond to threats quickly and effectively with our advanced detection and response capabilities.
Extended Detection and Response (XDR)
Unify security data from multiple sources for faster detection and response.
Endpoint Protection (EPP/EDR)
Protect your endpoints with our comprehensive EPP and EDR solution.
Features Explained
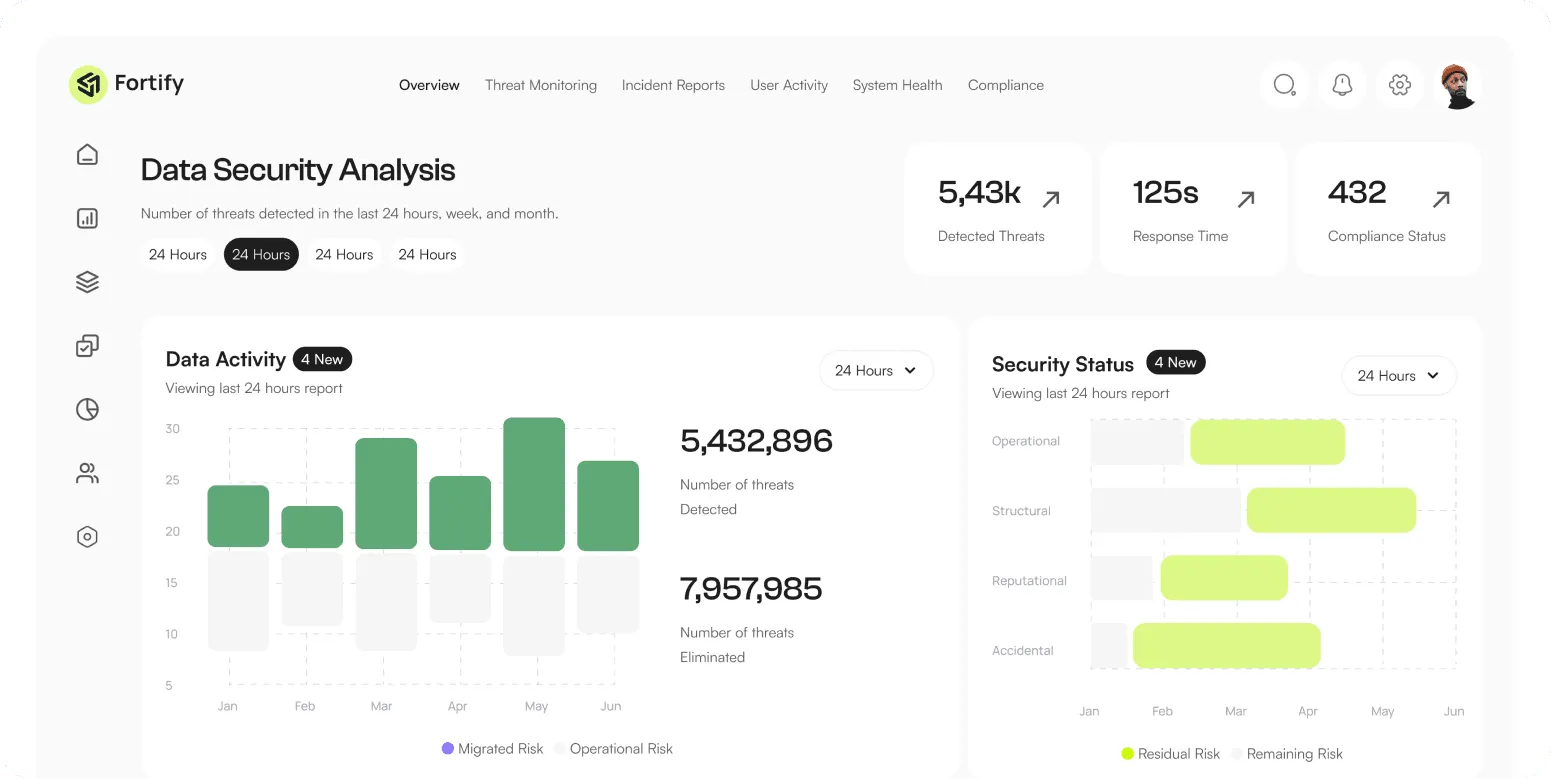
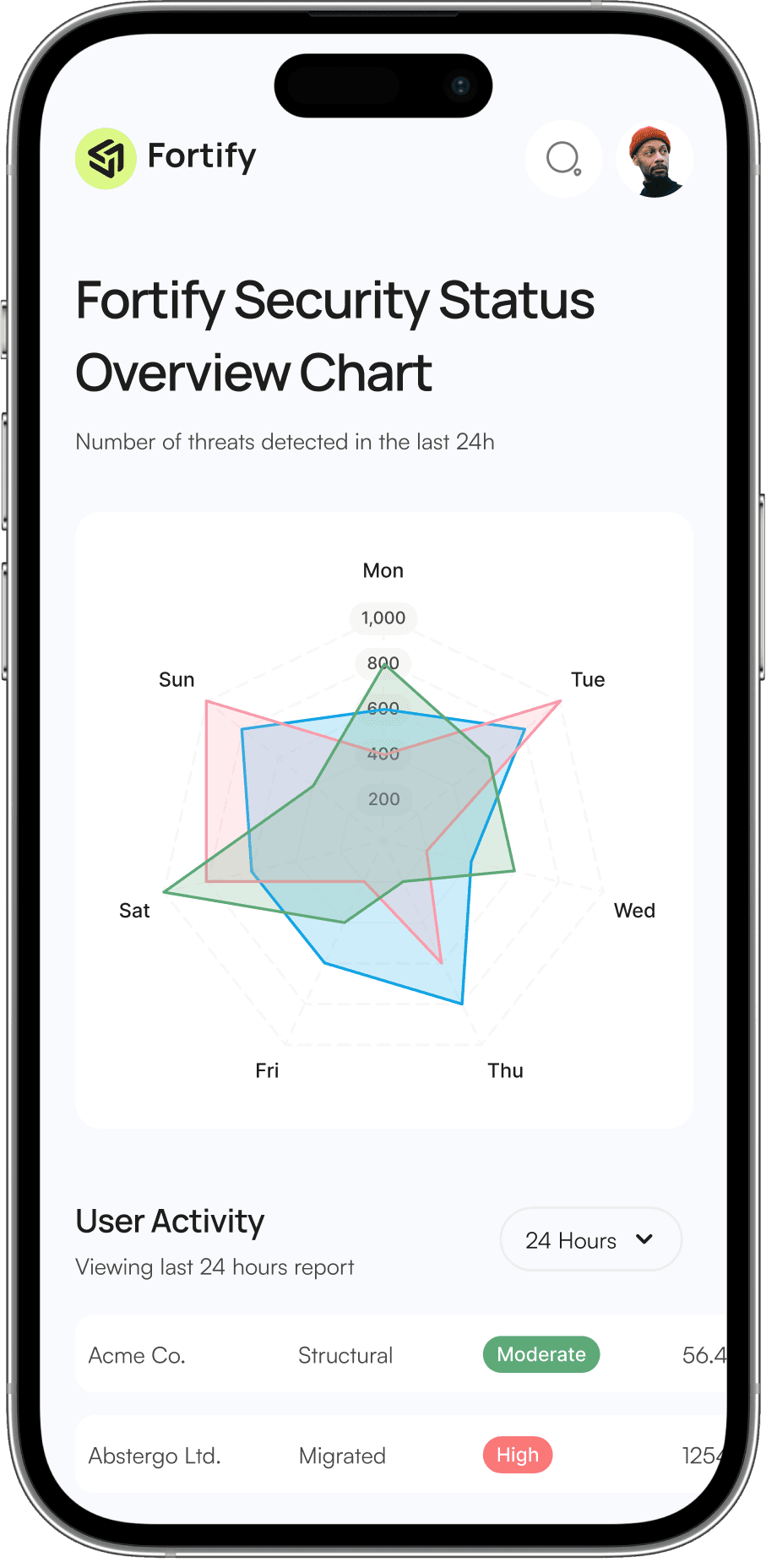
Interactive Chart Displays Key Metrics and Trends.
Your Trusted Partner in Data Protection with Cutting-Edge Solutions
for Comprehensive Data Security.
Security Status Indicator
Displays the current security status of your organization with a clear color-coded indicator.
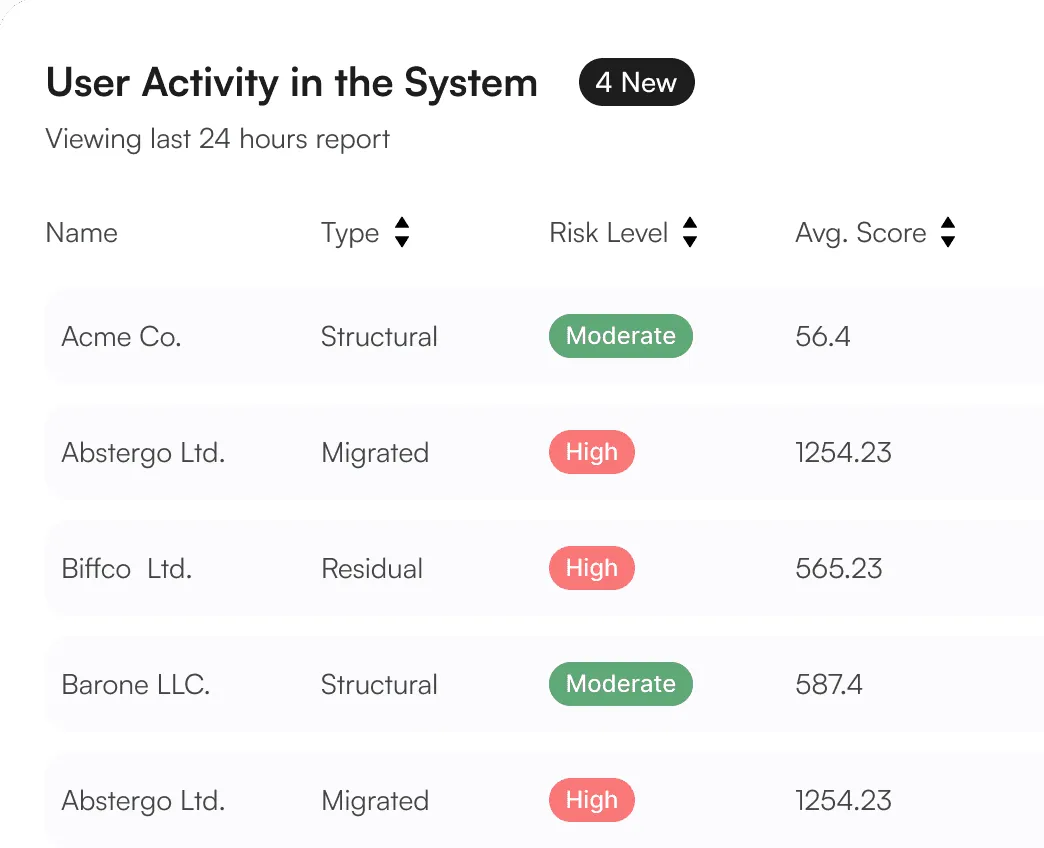
User Activity Monitoring
Highlights the most frequently accessed sensitive files or databases and the users involved, ensuring transparency and control over critical data.
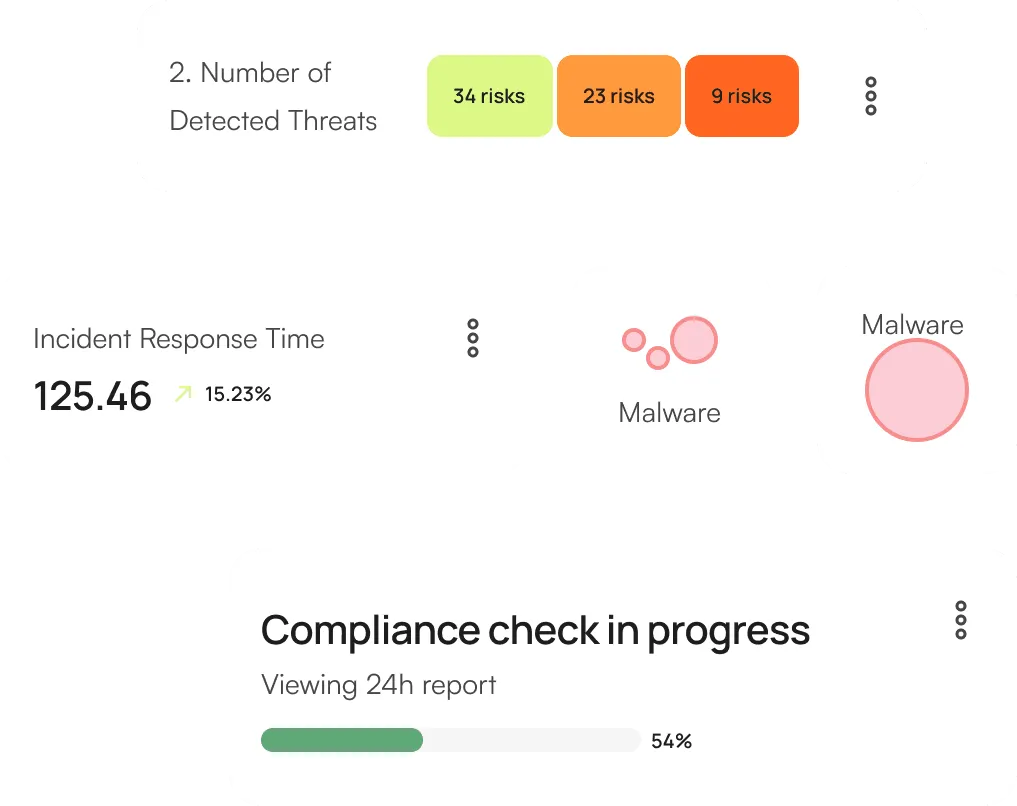
Threat Landscape Overview
Breaks down the threats by type (e.g., phishing, malware, ransomware) to give a detailed overview of the threat landscape.
Data Access Monitoring
Highlights the most frequently accessed sensitive files or databases and the users involved.
Incident Management
Lists the number of active security incidents currently being addressed.
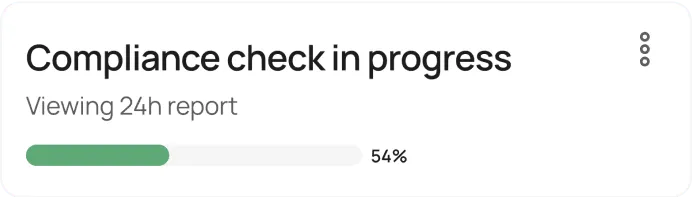
Compliance Monitoring
Our system continuously monitors your network and data environments for any suspicious activities.
Pricing & Plan
Choose a suitable plan
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Basic Plan
Ideal for small businesses or individuals looking to secure their data with fundamental protection features.
- Firewall-as-a-Service (FWaaS)
- Secure Web Gateway (SWG)
- Intrusion Prevention System (IPS)
- DNS Security (DNS)
- Remote Browser Isolation (RBI)
- Cloud Access Security Broker (CASB)
- Data Loss Prevention (DLP)
- Zero Trust Network Access (ZTNA)
- AI Security (AISEC)
- Extended Detection and Response (XDR)
- Endpoint Protection (EPP/EDR)
Premium Plan
RecommendedPerfect for medium to large businesses requiring security features and priority support.
- Advanced Threat Detection and Remediation
- Real-Time Alerts and Reporting
- Continuous Data Backup and Restore
- 24/7 Priority Support
- Multi-User Licenses (Up to 10 Users)
12,000+ Happy Customers
Customer Reviews
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Implementing this data security solution has been a game-changer for our company.
The real-time threat detection and automated response features have significantly reduced our risk exposure. We now feel more confident than ever about our data security posture.

IT Director at HealthCare
The granular access controls and detailed user activity tracking have given us unparalleled visibility.
The granular access controls and detailed user activity tracking have given us unparalleled visibility into our system's security. This platform has helped us maintain our data.

CTO at Tech Innovators Inc.
The comprehensive risk analysis and impact visualization tools are exceptional.
The comprehensive risk analysis and impact visualization tools are exceptional. We can quickly identify and mitigate potential threats before they become serious issues.

COO at Financial Services Group
Secure Your Data with SecureTrustCyber Protection Solution
Allows you to set thresholds for security parameters and receive real-time alerts when these thresholds are breached.
Get Started